An introduction to CAD security
A globalized world continues to bring major benefits to progressive companies around the globe. Supply chains have opened up, allowing companies to create complex products to meet the increasing demands from the market.
This same inter-connected world has laid the foundations for an increase in security threats, both in terms of frequency and severity. The result? Companies spending more time, effort and money to ensure intellectual property (IP) and proprietary data remains secure.
Lifecycle Insights’ 2022 CAD Security study seeks to explore these vulnerabilities facing manufacturers on a global scale. The findings in the study confirm manufacturers must seek to take steps to prevent the loss of engineering data and protect their IP. Additionally, manufacturers are thankfully taking security threats seriously; they are changing processes to implement industry-recommended strategies in order to protect themselves.
Preventing the loss of engineering data
A by-product of ever increasingly complex project designs is the increase in amount of CAD data generated. The amount of data generated has always been monumental, but with the need to ensure a product design is perfect, design engineers will tend to iterate and refine a design before it is complete. This is before you even consider the final Bill of Materials (BOM), numerical control (NC) machine codes and product and manufacturing information (PMI). Therefore, a CAD security vulnerability could risk issues to the design and development of any project such as lost design time and a significant loss in revenue.
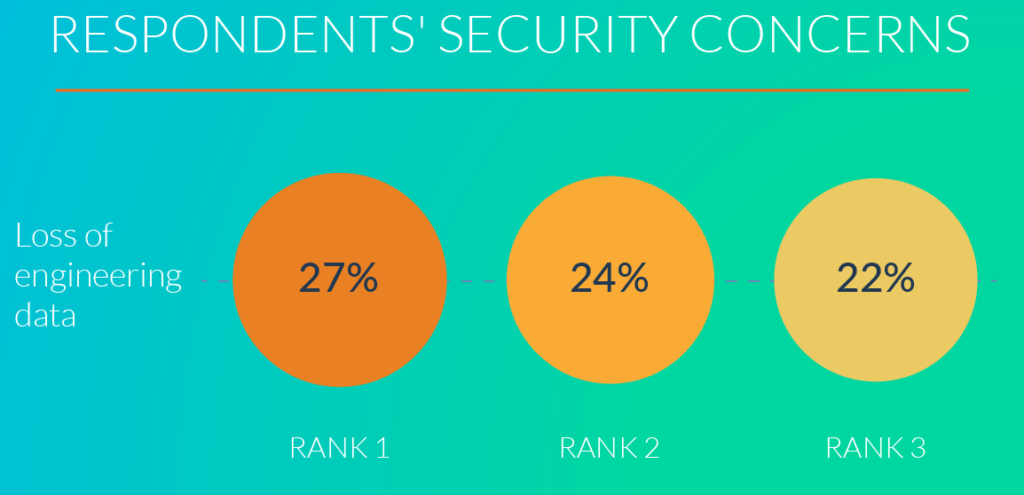
With this in mind, it will come as no surprise that 73% of respondents in the Lifecycle Insights report cited the loss of engineering data as one of their three top security concerns. Company’s that are hit with the loss of data need to spend time recreating it; this doesn’t even take into consideration the potential to start from scratch if product designs are brand new. As a result, productivity takes a significant hit, workforce morale decreases and, ultimately, product releases encounter significant delays.
Protecting your IP
You may not have realized, but a large amount of digital data serves as IP for organizations developing engineering products. IP can come in the form of sensitive documents, multiple iterations of CAD. When you strip it back to the barebones, protecting IP is absolutely essential to the long-term health of any organization; CAD data is connected via a digital thread, so any security breach significantly increases the chances of lost IP.
What is Intellectual Property?
“Work, data or a new creation in which a company has rights to, whereby they can apply for a patent, copyright or trademark”
It’s a key concern organizations recognize for their CAD security which could threaten the status quo. 54% of respondents rank the loss of IP as a top three concern, whilst it ranked second as the most important security concern. Companies designing innovative and significantly differentiated must protect their invaluable intellectual property to stay ahead of the competition.
A globalized marketplace may make it easier for products to reach wider markets, but a loss of IP can undermine time and money spent on research and development. Additionally, ‘copy cat’ products based on stolen IP can hit markets, damaging the reputation of innovative companies and significantly impact on their success.
Reduce ransomware attacks
A ransomware attack differs from an IP theft, but both can cause serious damages for organizations. Software users can inadvertently be the ones to infect their organizations’ systems; a ransomware attack causes data to become encrypted, and the only way for it to be encrypted is to pay a ransom to acquire a key from the perpetrator. Unfortunately, a CAD file from an unknown source can unknowingly be accessed by an engineer, affecting the companies’s systems as a result.
It’s the reason why ransomware attacks are becoming more common across the globe; thousands of attacks occur in the United States alone.
It’s a problem that more executives are recognizing, due to their devastating nature on CAD security. Ransomware can completely block companies’ access to essential data throughout the digital thread; whether that’s CAD files, NC machines codes, and other PMI, they are all in the firing line. Perpetrators will demand organizations pay a ransom to regain access to secure data. Combining all these elements means production can grind to a halt, and monetary finances are potentially needed to pay the perpetrator.

What’s the outlook towards CAD security
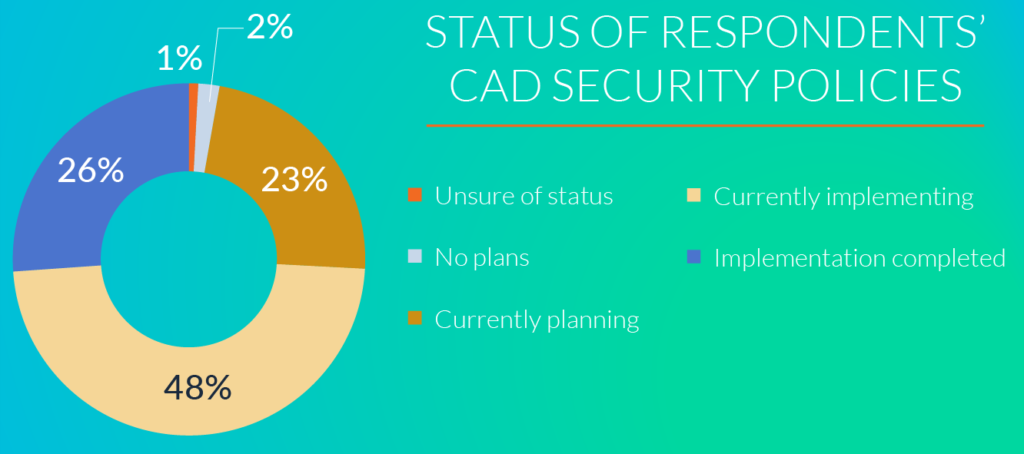
Considering the several ways in which an organizations’ CAD security is compromised, it’s essential that they begin to implement strategies that protect their prized assets. Thankfully, there is a concerted effort across the board to be pro-active in avoiding these crippling security issues; 97% respondents within the Lifecycle Insights CAD security study are in some form adopting new security policies.
There isn’t a prescribed approach organizations should take when implementing a new security strategy. Having said that, many engineering companies are re-evaluating the security features within their chosen CAD solution. These packages need to be completely secure due to the role they play throughout the whole digital thread. Without a secure CAD solution, organizations leave themselves exposed to ransomware attacks, IP theft and the possibility of losing their competitive edge.
What do the most progressive companies gain from strong CAD security policies?
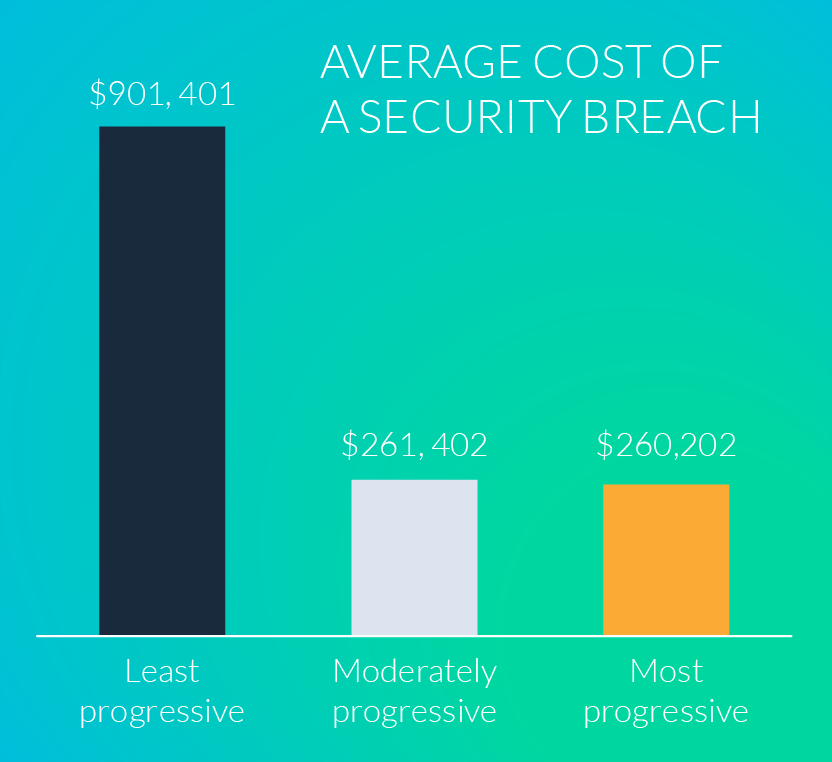
It may be an obvious statement, but organizations implementing a level of security into their processes experience significant gains. This is completely dependent on how progressive organisations choose to be with their CAD security strategy; the least progressive organisations spend $901,401 on average for a security breach, whereas moderately progressive organisations spend $261,402; a 71% decrease.
The most progressive companies see the most exponential gains when implementing security strategies. The average number of yearly ransomware attacks drops by 14%, yearly IP compromises by 25% and data loss through a security breach by 25%. A more aggressive approach to eliminating security issues therefore enables these organizations to increase productivity, as engineers don’t need to waste time recreating lost CAD data. Additionally, companies can work in confidence with their data, knowing that their IP is less vulnerable to attacks; combine this with lower costs and higher profit margins ensure these companies can improve their competitiveness and maintain an advantage.
The typical strategies pursued to mitigate security risk
Let’s explore what exactly constitutes a sound security strategy for organizations that work with CAD data. The Lifecycle Insights Security Study suggests there’s no one dominating strategy, but there are a few top strategies that companies are implementing. Like any best practice, companies ensure that they are doing their due diligence upfront with prospective CAD partners. Organizations are looking for CAD partners that can demonstrate whether their solution has standard certificates, recognized across all industries on a global scale.
Evaluations of these CAD solutions before implementation is critical; it enables organizations to determine whether their security policies are well aligned and begins to build up early trust and synergies. No wonder then that 86% of the most progressive companies adopt and practice this strategy!
Perpetrators are cunning and have multiple ways of infiltrating an organizations’ systems. Thankfully, CAD solutions regularly update their solutions to ensure potential security breaches are kept at bay. These updates generally cover new features and bug fixes, but will also include minor and major security updates. Organizations will look for this during the initial search of a new CAD solution; they must ensure their data is continuously protected, enabling the organizations to maintain productivity by reducing time and effort combatting a data breach. Thankfully, 70% of the most progressive companies are already addressing this.
Siemens ProductCERT security strategy
Siemens ProductCERT is a dedicated team of seasoned security experts that manages the receipt, investigation, internal coordination, and public reporting of security issues related to Siemens products, solutions, or services
Conclusion
An inter-connected world opens up many possibilities for all organizations. Unfortunately, the same can be said for perpetrators and their ability to commit security breaches. The Lifecycle Insights CAD security study has revealed the organizations are taking this threat seriously. Not only are they just identifying a secure CAD solution, but they are implementing industry-recommended strategies and regularly checking their security protocols are up to standard. The result? Organizations spending less time re-creating lost CAD data and more time focusing on the designs that matter the most.
Stay up to date with the Siemens Software news you need the most. Get Started