Has enabling remote work during this pandemic increased cyber threats to your engineering data?
Due to the COVID-19 pandemic, many firms have moved to remote working arrangements that are based on remote access to systems and data that may be critical. Given the widespread shift to working remotely for a prolonged time, new and more cyber-attacks are increasing. For Engineering companies, their technology and intellectual property is the heart of the business. A cyber-attack can disrupt the business severely and worsen the already challenging economy of the company. Firms should consider implementing the necessary steps to protect their Engineering IP data. IT is responsible for protecting IT systems like emails and drives from hacks, but engineering should consider adding an extra layer of security in case IT systems are compromised. Data is becoming day by day, the company’s biggest asset as well as risk. Easy access and scalability of cloud platforms mean more data. Just compare the amount of personal data we used to store digitally 10 or 20 years ago and now. Below are some the recent observations from various organizations post covid.
Statistics about cyber attacks
1. Cyber-Attacks Up 37% Over Past Month as #COVID19 Bites (info security)
2. Online threats have risen by as much as six-times their usual levels over the past four weeks as the COVID-19 pandemic provides new ballast for cyber-attacks (Cloudflare)
3. Phishing attempts have soared by over 600% since the end of February ( Barracuda Networks)
4. Hackers attack every 39 seconds, on average 2,244 times a day. (University of Maryland)
5. The average time to identify a breach in 2019 was 206 days. (IBM)
6. In the 2019 DBIR, 94% of malware was delivered by email. (Verizon)
7. 34% of data breaches involved internal actors. (Verizon)
8. The average cost of a ransomware attack on businesses is $133,000. (SafeAtLast)
9. 48% of malicious email attachments are office files. (Symantec)
10. Financial and Manufacturing services have the highest per cent of exposed sensitive files at 21%. (Varonis)
11. The cost of lost business averaged $1.42 million. (IBM)
12. Only 5% of companies’ folders are properly protected, on average. (Varonis)
13. 62% of businesses experienced phishing and social engineering attacks in 2018. (Cabinet Solutions)
14. The average lifecycle of a breach was 314 days (from the breach to containment). (IBM) 15. In 2016, Uber reported that hackers stole the information of over 57 million riders and drivers. (Uber)
16. In 2016, 3 billion Yahoo accounts were hacked in one of the biggest breaches of all time. (NY Times)
17. The average cost of a data breach is $3.92 million as of 2019. (Security Intelligence)
18. IoT devices experience an average of 5,200 attacks per month. (Symantec)
Which data is at risk?
The hackers are interested in the intellectual property of a company which can be in the form of drawings, blueprints, documents, process charts, instructions, assembly methods and many more forms.
All that data which describes your unique product can be at risk. Your R&D department may have spent years to develop these technologies and products, and the hackers want to sell them to pirates, competitors or harass you for money. Apart from that, they may want to disrupt business by hacking emails and reaching your customers and suppliers. With advanced data sorting algorithms, they can quickly sort a huge amount of data and classify it as per sensitivity.
Reasons for cyber-attacks?
Apparently, it is believed that it is easy to acquire engineering data because of the complex supply chain and collaboration requirements to manufacture products. Data needs to be accessible to different internal and external departments and actors. Suppliers, for example, needs information like drawings and specifications to make parts. Below are the top four reasons for a data breach:
1. MS Office files over emails
Engineering data are maintained in excel, word or other office formats and exchanged over emails. 48% of malicious email attachments are office files, according to Symantec. These malicious office files blend easily into everyday business data. When Emails are used extensively to share engineering data, the risk of cyber-attack increases exponentially. Your IT department can get overwhelmed with the amount of data shared over emails and shared drives that it becomes impossible to track suspicious actions.
2. Data spread all over
Companies who do not use a PDM or PLM system to manage Engineering data at one place have their data spread across all over in shared files, emails, paper-based and other types of storages and exchanged over emails or shared folders. This is very risky as almost all employees end up getting access to critical files. 53% of companies had over 1,000 sensitive files open to every employee (Varonis) while 34% of data breaches involved internal actors (Verizon). Folder level access is either ON or OFF type and does not give the possibility to control access as per role and department. For example, designers need access to all data in a design folder, but purchase might only need access to 2D drawings of particular function or area he/she is responsible for. Maintaining these complex access rules is difficult at the folder level.
3. Outdated version of software’s
Outdated versions are a rich source for cyber attackers. Also, old versions of supporting software with PDM/PLM system like JAVA, MS Office, Database, OS etc. are vulnerable. Hackers get enough time to find loopholes in these older versions. The suppliers always tend to fix these loopholes in the latest versions. Not all systems can be updated overnight like windows update, hence upgrade must be a regular budgeted activity for business and taken up as a business risk and OPEX. We have offered long term upgrade contracts to customers to enable them to upgrade regularly, avoiding the hassle for frequent approval cycles and having an expert team ready to make it foolproof. There are certain state-sponsored hacking groups which specifically target this software and are very difficult to identify.
4. Remote working
Work from home due to coronavirus is essential, but most of the home networks are not sufficiently protected. Employees working from home may not be aware of potential loopholes which cybercriminals target. Also, there is increased information transfer over emails. IT department might have also relaxed some thresholds to enable work from home or remote. All this increase cyber risk multiple times in the current situation. Nobody had planned for work from home on such a large scale, and some of the companies struggle to get work done remotely due to insufficient setup.
Consequences of cyber-attacks?
Consequences of cyber-attacks are huge and can be devastating for the company. It is not only engineering data which will be compromised, but the hack provides entry to all of the company data:
1. Financial loss:
Direct loss due to ransom payment, production stoppage, order cancellation, delivery slippage, lost business hours. Indirect losses due to lost morale, productivity dip and psychological reasons. The average cost of a malware attack on a company is $2.6 million. (Accenture). The cost of lost business averaged $1.42 million. (IBM)
2. Busines Disruption
Just last year, a Saudi Arabian petrochemical manufacturer was targeted by malware believed to steal data and put a complete halt in operation, and to cause an explosion with potentially devastating consequences reports manufacturing global magazine. The malware targeted the plant’s industrial control systems and was designed to stop any automated equipment from going beyond the safe operating conditions and to override the machine’s initial codes.
3. Loss of reputation
Customers and suppliers rely on each other to keep data secure and guard the gates of their ecosystem. Any breach will make them sceptical and cause trust issues. Reputation in the general public is also affected, affecting sales and share prices.
4. Loss of IP data
Technology and Intellectual property is the biggest asset for an engineering manufacturer. If it is fallen in wrong hands, it can be misused for piracy, harassment, unwanted or unethical use. It can compromise the niche position in the market. Defence & other technology can be misused against humanity.
5. Legal fines and punishment
Data privacy is the responsibility of the owner company, and loss can lead to fines based on the nature of data. Businesses spent $1.3 million on average to meet compliance requirements and are expected to put in an additional $1.8 million. (IAAP) Personal information or export control technology can lead to heavy fines for the company. These fines can lead to insolvency for some growing companies. Equifax was found liable for their 2017 breach and was fined $425 million by the Federal Trade Commission (FTC) in 2019. (FTC).
What can we do to protect engineering data?

With the advent of new technology, cyber-crime is also getting sophisticated. Cybercriminals are inventing new methods to breach in and cause disruption to the business. Businesses have to be proactive and regular to prepare and avoid such attacks constantly. Below are some of the measures a company can implement to secure its most important IP data.
1. Secure all engineering data in a single source/system
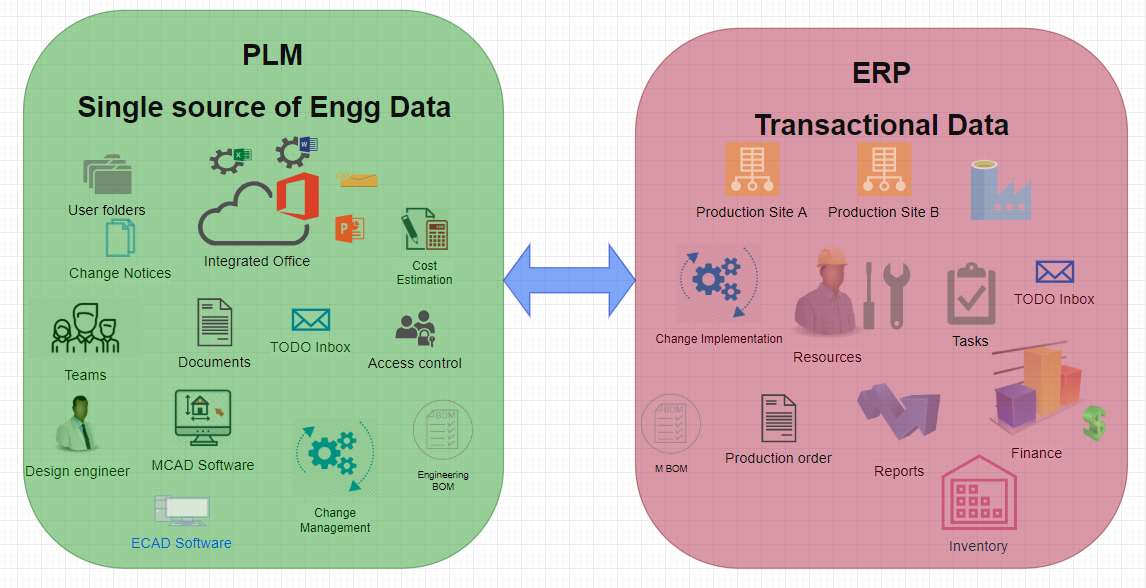
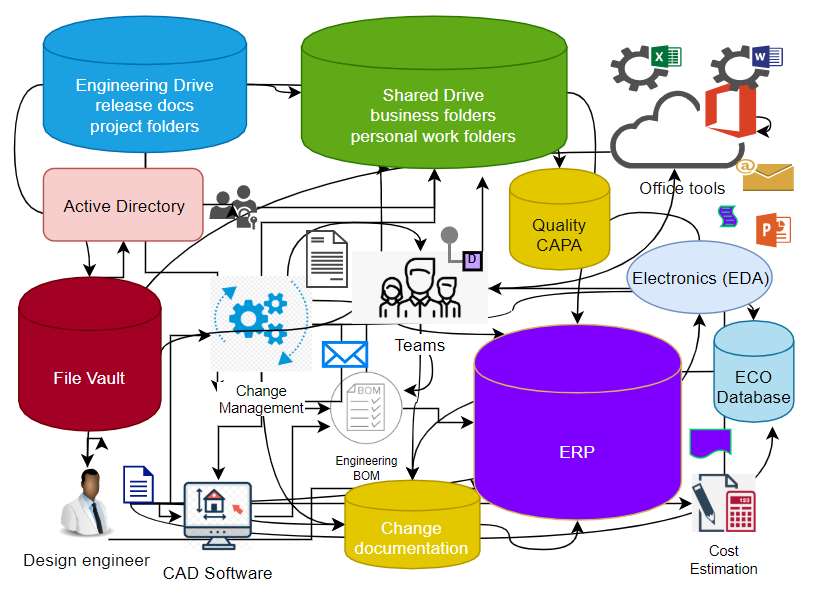
Modern-day PDM/PLM systems are designed on security principles and provide a lot of configuration capabilities to give access to data in a controlled fashion. A lot of roles like the Basic user, Designer, Manager etc., can be set up, and access rules can be defined accordingly. Automatic logging and admin controls make it possible to monitor a large amount of data and suspicious activities. It is easy to protect one source rather than data spread all over. These systems also provide the ability to share encrypted data without using emails and attachments, both internally and externally. These systems provide an additional layer of security in case IT system like emails are compromised. IP data can be tagged, and special access rules can be applied to make it selectively accessible. Export rules or workflows can be defined so that all data export out of the system can be logged and if necessary, approved before export. All this makes it more secure to work on these systems remotely as well as makes it super easy to collaborate remotely. All involved users can log in to system and access and see data as per their roles without import /export/email/hard-drive saves making it robust. There are advanced solutions available for companies who have strictly export-controlled defence or biotech data which is regulated heavily.
2. Security testing
Test your data security by simulating use cases to find loopholes and actively close them. Take help from Product data management experts and cybersecurity experts to check and improve data security.
3. Upgrade and maintain the latest supported version of CAD/PDM/PLM system
Applying maintenance patches and upgrades should become second nature of the admin department whether users like it or not. Often the problem is with the budget. This should be budgeted as operational expense and risks should be explained to management. It is not only engineering data, but the whole company can be affected due to cyberattacks.
Monitor and review privileges at regular intervals. Temporary privileges stay and accumulate. People end up getting a lot of unnecessary access over time in a folder-based access system. This needs to be constantly reviewed, and if possible, a proper data management system should be used.
5. Backup and restore exercises at regular intervals.
This should be a regular admin activity. Many times this falls between chairs between engineering and IT. Engineering data admins assume IT have backups and IT assumes engineering has backup. A recovery exercise is a must at the same interval as fire exercise.
6. Organisation incident response plan in case of cyberattacks.
Your life will become easy if you have the plan in case something goes bad. Following plan and testing is key to avoid a lot of damage.
7. Use system for exchanging files and collaboration instead of emails
Email data exchange is the biggest source of cyber-attacks. If possible, use PDM/PLM system functionality to exchange data. Email can only point to data like part numbers, descriptions, but actual data should be available to uses only after login to the system. All can see the data at one place instead of sending it backwards and forwards.
8. People are always a weak link.
Educate people and manage access. Huan errors cannot be avoided hence use system and automation to assist people. Also, regular education on data security is essential to avoid problems, especially with the older staff. Rewards or recognitions for identifying or informing possible loopholes is also a good way to motivate people. Every company needs to create an environment of digital security these days as we have already entered the data age.
9. Management focus and awareness.
Data Security is everybody’s concern. Given the financial and other consequences, data security is not just IT responsibility. Management should make it a business risk and track it actively as part of a business review. Intellectual property can erode the bottom line easily and put the company in a serious problem overnight. The disruption ability of cyberattacks demands full support from every employee to avoid and counter. Your IT department might be already overloaded due to work from home/remote challenges and support. Giving additional cybersecurity responsibility to your company fire marshals or similar roles is a good idea to help your IT.
Source: PLM Nordic

Don’t hesitate to contact Thanh for advice on automation solutions for CAD / CAM / CAE / PLM / ERP / IT systems exclusively for SMEs.
Luu Phan Thanh (Tyler) Solutions Consultant at PLM Ecosystem Mobile +84 976 099 099
Web www.plmes.io Email tyler.luu@plmes.io